#Loading MSG file
Explore tagged Tumblr posts
Text
+[ERROR MSG : FILE LOADED INCORRECTLY.]
╌╌╌╌╌╌╌╌╌╌╌╌╌╌╌╌╌╌╌╌╌╌╌╌╌╌╌╌╌╌

[send error report?] ﹂ [yes] | no ﹂ [error report sent to administrator] ﹂ [ok]
╌╌╌╌╌╌╌╌╌╌╌╌╌╌╌╌╌╌╌╌╌╌╌╌╌╌╌╌╌╌
++[MSG : the following file may be loaded incorrectly. we apologise for any errors!]

🗀 C:/PROJECTS/MYWORK/ONESHOT/NEVERJUSTFRIENDS [projects] ﹂ [my work] | in progress | favourites ﹂ all | multi-chapter | [one-shot] | blurb | head-cannons ﹂ [never-just-friends]
+[MSG : the following content is NSFW.]

▇▇▇▇▇▇▇▇▇ [CORRUPTED]
▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇ He, in turn, slips his hand past the waistband of your sweats and underwear, immediately running his long fingers through your folds. Noah breaks the kiss to rest his forehead against yours as you both pant.
"So wet for me already," he teased, "have you been thinking about me?" Your breath catches in your throat as he begins to circle your clit precisely where you like it with two fingers. "Hm? You been thinking about how good I can make you come?"
▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇
"Does that feel good, baby?" he brushes your hair back behind your ear and cups the side of your face, tilting it up to meet his. You feel his hot breath against your lips when he speaks, "are you gonna come for me already?"
You can only whine and nod, the hand that was ▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇
[CORRUPTED]
▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇▇
[CORRUPTED]
#C:/PROJECTS/MYWORK/TEASER#I POSTED THIS ACCIDENTALLY AGAIN#noah sebastian smut#noah sebastian x reader#noah sebastian fanfic#noah sebastian
20 notes
·
View notes
Text
Home >> Departments >> Research >> Subjects >> Intelligent Subjects >> Subject R-0808
LOADING . . .
LOADING . . .
FILE OPENED
rue_xoxo
name Rue
prns she/they [ no preference ]
age 16 [10/02/2008]
fav color blue!! [ powder ]
fav movie[s] Labyrinth - Bohemian Rhapsody - The Crow - CATWS - Lisa Frankenstein - Twister [1996]
fav show[s] Supernatural - Charmed
fav book[s] PJO - Carrie - Vampire Academy - Danger Days - National Anthem
fav band[s] My Chemical Romance - Fall Out Boy - Panic! At The Disco - Sublime - Ramones - Misfits - Korn - Kittie - Jack Off Jill
hobbie[s] guitar - writing - art - reading - baking - cooking
sports/activities drama - choir - forensics - scholars' bowl
subject rundown (penned autobiographically)
Hiii!!! I'm Rue. I do art and stuff and I'm super into music and movies. I live in the Midwest so uhhh sadly there is little alternative fashion to be found in thrift stores otherwise I'd be serving. Otherwise, have a good day!!! :3
Rue's Tags Info
P.S. - I reeeaalllyyy like MCR.
P.P.S. - I do lots of art. Please harrass me to post it <3
P.P.P.S. - did you know P.S. stands for Post Script? Wild!
P.P.P.P.S. - my art account is @xoxoidrawthingz
P.P.P.P.P.S. - pls dm me if you want to talk (i'm too scared to msg u first prolly)
11 notes
·
View notes
Text
One of my most favorite scenes from Eureka must be Jo's dream from the episode "Noche de Suenos." Here is that amazing scene for all of you to watch!
Link for the video on YouTube if it doesn't load! (Might be region locked. If neither work, please msg me, and I will give you the file!)
#so for context everyone thought is was Fargo's dream but we later learn it is Jo's#Also everyone is sharing dreams as well#that seems important to mention#eureka#eureka tv show#a town called eureka#adiraofthetals
2 notes
·
View notes
Note
I’m so glad the whole blocking thing was figured out, some people need to touch grass for real! I love your gifs (especially the variety!) and am glad you’ll keep making them! I’ve got a few gif-related questions if that’s ok? Whenever I make gifs, I find it basically impossible to have much more than about 35 frames without going over 3mb (and like we’re talking super basic gifs, nothing fancy), so how are people getting so many gorgeous gifs (that seem fairly long) in one post?? And last question, how to you know who/what to tag? I tag the show/character/actor etc, but when it comes to all the extra ones, I’m lost. Anyway sorry for the long msg haha, you don’t have to answer, just wanted to say happy you’re feeling better and I wish sharp legos to the bare feet of whoever is being unwelcoming in the gif community
hey anon!
tumblr drama, who needs it eh, seriously 🙃
tysm💛🥰 i love having a variety to gif it keeps me from getting bored. of course it's okay to ask, i'll try and help in my incoherent way if i can lol.
[This is assuming like me you use photoshop to make your gifs and are working with 1080p files. I usually make big gifs so it's pretty much 540x430/540x450 and then 540x500/540x540 when necessary. The rule being the bigger the gif dimension, the higher the download quality/sharpening/colouring = the bigger the final gif size will be.]
I usually load around 100-200 screencaps into ps, do all colouring/sharpening and then deal with getting it under the gif limit which is 10mb.
I'll use some examples of gifs I made today and the results for me: both are made with 1080p files and coloured/sharpened the same.
GIF A: 540X350 dimension, 35 frames 4.4mb

GIF B : 540x450 dimension, 35 frames, 5.8mb

To the second part of your ask who to tag: You can look at my gifs and see the ones I usually tag for reference. I tag gifmakers and source blogs and then [insert either show/character name... then edit]
With the gifmaker tracking tags, I'll see who is into the same shows as me, has a tracking tag usually found in the bio, makes gifs for the same fandoms and tag them and some will reblog any media.
With the source blogs they will reblog all film/television etc.
So if you gif similar stuff to me then just tag the same people, if not have a look around your fandoms for people who have tracking tags you can even send them an ask, saying do they mind being tagged.
I'll pop some below off the top of my head that are pretty great at reblogging things in general:
GIFMAKER TAGS
userrlaura/userrobin/usermandie/usergiu/nessa007/usersco
userholtz/userdiana/useradie/useraurore
SOURCE BLOGS
dailyflicks/userstream/useroptional/usertelevision/userblorbo
tvedit/userbbelcher/tvandfilm/chewieblog
EDIT TAGS
for example for my buffy gifs i will tag either: dailybuffysummers/btvsedit
for my evan buckley gifs
evanbuckleyedit/911edit/evanbuckleysource
#soph asks#i hope this was in some way helpful to you and good luck with your gifmaking!!!#i hate trying to explain myself in written form i'm so much better with my words.
3 notes
·
View notes
Text
Free Methods to Convert OLM Files to PST for MS Outlook in Easy Steps

Method 1: Manual Export Using an IMAP Account
This method requires configuring an IMAP account, such as Gmail, to act as an intermediary between Mac Outlook (OLM) and Windows Outlook (PST).
Step-by-Step Process:
Set Up an IMAP Account:
Open Gmail, go to Settings > Forwarding and POP/IMAP, and enable IMAP.
Open Mac Outlook, navigate to Outlook > Preferences > Accounts.
Add a new account by entering the IMAP account credentials.
Synchronize OLM Data with IMAP:
Create a new folder within the IMAP account in Mac Outlook.
Drag and drop your emails from Mac Outlook to this IMAP folder to start syncing.
Access Data from Windows Outlook:
After the sync is complete, open Windows Outlook.
Add the same IMAP account to Windows Outlook. You should now see all your emails synced.
Move emails from the IMAP folder to a new PST file by navigating to File > Open & Export > Import/Export and selecting Export to a file.
Method 2: Export Methods Using Microsoft 365
If you have a Microsoft 365 subscription, you can use it to transfer emails between Mac Outlook and Windows Outlook.
Steps to Follow:
Configure Mac Outlook with Microsoft 365:
Open Mac Outlook and set up Microsoft 365 as a new account under Preferences > Accounts.
Drag and drop OLM data into the Microsoft 365 mailbox.
Access Data on Windows Outlook:
Log into your Microsoft 365 account in Windows Outlook. All OLM data should now be available in the Microsoft 365 mailbox.
Copy these emails to a PST file in Windows Outlook to complete the conversion.
Method 3: Exporting via Apple Mail and Importing to Windows Outlook
To migrate Apple Mail to Windows Outlook, first export emails from Apple Mail as MBOX files. Then, use an MBOX to PST converter to convert the files.
This method is more involved and ideal if you need to convert only a few emails or folders.
Instructions:
Export Emails from Mac Outlook: Open Mac Outlook, select the emails or folders you want to export, and export them to .mbox format.
Import MBOX to Apple Mail: Open Apple Mail, go to File > Import Mailboxes, and select the MBOX file. This will load your Mac Outlook emails in Apple Mail.
Use EML Format to Save Emails: Drag each email from Apple Mail to a new folder to save them as .eml files.
Import EML Files into Windows Outlook: Open Windows Outlook, and use a third-party tool to import EML files into PST format, as Outlook does not natively support EML to PST conversion.
Method 4: Using an OLM to PST Converter Tool

Many professional OLM to PST converter tools offer free demo versions, which can be used to convert a limited number of emails or files.
Download a Free OLM to PST Converter: I have explain some best OLM to PST converter tool that offers a demo version (e.g., SysVita OLM to PST Converter, ATS OLM To PST Converter & Vartika OLM to PST Converter).
1. SysVita OLM to PST Converter
Description: SysVita OLM to PST Converter efficiently converts Mac OLM files to PST format, supporting bulk exports with all versions of Outlook and Windows. The software also allows for conversion to multiple formats like MBOX, EML, MSG, and supports direct export to IMAP and Office 365.
Pros:
Bulk export support.
Compatible with all Outlook and OS versions (Mac & Windows).
Includes a free demo version for testing.
Direct migration to IMAP & Office 365 accounts.
Cons:
Limited features in the trial version.
2. ATS OLM to PST Converter
Description: ATS OLM to PST Converter is a user-friendly tool that converts OLM files to PST, EML, MSG, EMLX, and MBOX formats. It doesn’t require Outlook installation and includes a preview feature to verify data before migration. This converter supports all versions of Outlook, from 2000 to 2021.
Pros:
Supports multiple formats: PST, MBOX, EML, MSG.
Preview feature for data verification.
No Outlook installation required.
Free demo for testing, with up to 30 items converted.
Cons:
Limited options in the free version.
3. Vartika OLM to PST Converter
Description: Vartika OLM to PST Converter is designed to convert OLM files from Mac to PST format for Windows Outlook users. This tool also supports conversion to formats like EML, MBOX, MSG, and Office 365. It includes advanced filtering to help you select specific data.
Pros:
Multi-format conversion options.
Advanced filtering for selective migration.
Direct export to Office 365 and Live Exchange.
Allows preview of email items before conversion.
Cons:
Limited options in the free version.
Each converter has unique strengths, so choosing the best one will depend on the volume of data, preferred formats, and additional migration options like direct IMAP or Office 365 compatibility.
Convert OLM to PST Using the Tool: Using a dedicated OLM to PST conversion tool is often the fastest, most reliable method, especially if you have a large number of files to convert. Here’s how to use an OLM to PST converter tool to seamlessly convert your Mac Outlook files to a format compatible with Windows Outlook.
Step-by-Step Guide:
Download and Install a Reputable OLM to PST Converter Tool:
Begin by choosing a well-rated tool with a free trial version, such as SysVita OLM to PST Converter, ATS OLM Converter, or similar.
Install the software on your Windows computer by following the setup prompts.
Launch the Tool and Import the OLM File:
Open the converter software and look for an option like Add File or Open.
Select the OLM file you wish to convert. Many tools also allow you to preview the contents before proceeding.
Choose PST as the Output Format:
In the export options, select PST as the desired output format. You may also be able to configure additional settings, such as preserving folder structure, filtering emails by date range, or converting only specific folders.
Select the Destination Folder:
Specify where you’d like the converted PST file to be saved on your system.
Begin the Conversion Process:
Click Convert or Export to start the process. The time required will depend on the size of the OLM file and the speed of your system.
Open the Converted PST File in Windows Outlook:
Once conversion is complete, open Microsoft Outlook on your Windows system.
Go to File > Open & Export > Open Outlook Data File, locate your newly converted PST file, and import it.
Conclusion
Converting OLM to PST manually can be a time-consuming process, especially for larger files. While free methods are available, they require multiple steps and some technical knowledge. If you regularly need to convert OLM files to PST, investing in a professional OLM to PST converter might be worth considering for a seamless experience.
#news#technology#olmtopst#OLMtoPSTConversion#hashtag#FreeOLMtoPSTMethods#ConvertOLMFiletoPST#MSOutlookOLMConversion#MacOutlooktoWindowsOutlook#IMAPOLMtoPST#Microsoft365EmailMigration hashtag#AppleMailtoOutlook#FreeOLMConverterTools#OLMtoPST hashtag#Step-by-Step hashtag#Guide
0 notes
Text

Stress
You write a script to automate sending daily email reports using Python. We'll use the smtplib library to send emails and the email.mime modules to create the email content. Here's a step-by-step guide:
Step 1: Install Required Libraries
First, ensure you have the necessary libraries installed. You can install them using pip if they are not already installed.pip install smtplib pip install email
Step 2: Set Up Email Credentials
You need to have the credentials for your email account (e.g., Gmail). For security reasons, it's better to store these in environment variables or a configuration file.
Step 3: Create the Python Script
Here's a sample script that sends an email report daily:import smtplib from email.mime.multipart import MIMEMultipart from email.mime.text import MIMEText import os # Function to send email def send_email(subject, body, to_email): # Email credentials email_address = os.environ.get('EMAIL_USER') email_password = os.environ.get('EMAIL_PASS') # Create the email msg = MIMEMultipart() msg['From'] = email_address msg['To'] = to_email msg['Subject'] = subject # Attach the body with the msg instance msg.attach(MIMEText(body, 'plain')) # Create server object with SSL option server = smtplib.SMTP_SSL('smtp.gmail.com', 465) server.login(email_address, email_password) # Send the email server.send_message(msg) server.quit() print("Email sent successfully") # Function to generate the report def generate_report(): # Implement your report generation logic here report = "This is a sample report." return report # Main function to send daily email report def main(): report = generate_report() subject = "Daily Report" body = report to_email = "[email protected]" # Change to the recipient's email address send_email(subject, body, to_email) if __name__ == "__main__": main()
Step 4: Setting Up Environment Variables
To keep your email credentials secure, set them as environment variables. You can do this in your operating system or by using a .env file with the dotenv package.
Using Environment Variables Directly
Set your environment variables:
On Windows:
setx EMAIL_USER "[email protected]" setx EMAIL_PASS "your_password"
On macOS/Linux:
export EMAIL_USER="[email protected]" export EMAIL_PASS="your_password"
Using a .env File
Create a .env file with the following content:[email protected] EMAIL_PASS=your_password
Then, update the script to load these variables:from dotenv import load_dotenv # Load environment variables from .env file load_dotenv()
Install the python-dotenv package if you use the .env file method:pip install python-dotenv
Step 5: Automating the Script Execution
To run the script daily, you can use a scheduler.
On Windows
Use Task Scheduler to run the script daily.
Open Task Scheduler.
Create a new task.
Set the trigger to daily at your desired time.
Set the action to start a program and browse to the Python executable, then add the script path as an argument.
On macOS/Linux
Use cron to schedule the script.
Open the terminal.
Type crontab -e to edit the cron jobs.
Add a new line for the daily schedule (e.g., to run at 7 AM every day):
0 7 * * * /usr/bin/python3 /path/to/your_script.py
Summary
Install required libraries using pip.
Set up email credentials securely using environment variables or a .env file.
Write the Python script to generate the report and send the email.
Automate the script execution using Task Scheduler (Windows) or cron (macOS/Linux).
This setup will ensure your script runs daily and sends the email report automatically. If you have any specific requirements or encounter issues, feel free to ask!
0 notes
Text
COM S 327 Programming Project 1.08 Loading Pokemon ´ solved
We’ve parsed in a number of data files that specify certain details about how to create pokemon. Now ´ we’re actually going to load them into our game. We’ll add the ability to encounter them, but we’ll save battling and capturing for next week. We’re going to simplify many of the mechanics of the pokemon main series games (MSGs) in our im- ´ plementation. The full mechanics are just too tedious,…

View On WordPress
0 notes
Text
COM S 327 Programming Project 1.08 Loading Pokemon ´
We’ve parsed in a number of data files that specify certain details about how to create pokemon. Now ´ we’re actually going to load them into our game. We’ll add the ability to encounter them, but we’ll save battling and capturing for next week. We’re going to simplify many of the mechanics of the pokemon main series games (MSGs) in our im- ´ plementation. The full mechanics are just too tedious,…

View On WordPress
0 notes
Text

eSoftTools Windows Live Mail Converter Software
Des - A stand-alone software called eSoftTools Windows Live Mail Converter can convert contacts, emails, and calendars from Windows Live Mail to a number of other formats, including Outlook PST, PDF, MSG, and EML. This utility may load emails into it by automatically locating where they are stored on the local system. With this software, users can convert EML files in mass. This tool offers a number of advanced features. The mail's metadata is kept intact as they are converted to any of the formats. The utility works with Outlook 2019, 2016, 2013, 2010, and other versions when converting EML files to PST. Files can be exported from Windows Live Mail conversion software in a safe way without being harmed or corrupted.
1 note
·
View note
Text
Programming Project 1.08 Loading Pokemon´ Solved
We’ve parsed in a number of data files that specify certain details about how to create pokemon´. Now we’re actually going to load them into our game. We’ll add the ability to encounter them, but we’ll save battling and capturing for next week. We’re going to simplify many of the mechanics of the pokemon´ main series games (MSGs) in our im-plementation. The full mechanics are just too tedious,…

View On WordPress
0 notes
Text
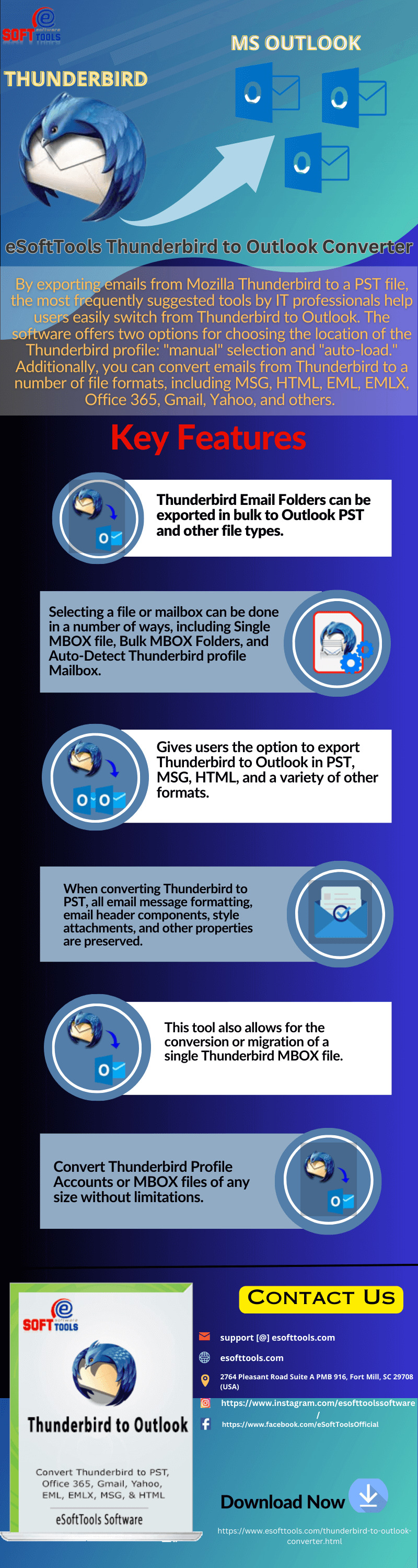
The most frequently recommended tools by IT specialists assist users in quickly switching from Mozilla Thunderbird to Outlook by allowing users to export emails from Thunderbird to a PST file. The software gives users the choice between "manual" selection and "auto-load" when it comes to selecting the location of the Thunderbird profile. You can also export Thunderbird emails in a variety of file formats, such as MSG, HTML, EML, EMLX, Office 365, Gmail, Yahoo, and others.
0 notes
Text
List Email Messages while Working with Pop3Client & MSG Contact to MHT using .NET
What's New in this Release?
Aspose team is pleased to announce the release of Aspose.Email for .NET 19.1, This release includes few enhancements in API and overall functionality of the API has been improved as a result of several bug fixes. This release includes few enhancements to the API’s functionality. These enhancements include listing messages while working with Pop3Client, loading and saving of VCF contact and reading of OLM and MBX files. This release includes several improvements in term of bug fixes, such as improved working with EWSClient while UpdateItems, Improved formatting of HtmlBodyText in output, Improved working with loading EML, Improved working with date in header using MapiMessage to display in MHTML output, Improved working with ImapClient.ListMessagesByPage, MSG contact to MHT conversion is enhanced, Improved working with signed MSG, MailMessage to HTML conversion is enhanced, VCF to MSG conversion is enhanced, PST to MBOX conversion is enhanced and MSG to MHTML is enhanced The main bug fixes & improved features added in this release are listed below
Pop3Client.ListMessages taking too much time
Unable to update email using EWSClient.UpdateItems
Loading and saving VCF contact skips some information
No bullets added to the output of HtmlBodyText
MailMessage.load throwing exception with EML Bug
Update date in header using MapiMessage to display in MHTML output
ImapClient.ListMessagesByPage retrieves last email even if the page does not exist
MSG contact to MHT conversion issue
MapiMessage.fromMailMessage throws exception
Issue while reading MBOX file
Empty body in a signed MSG
MailMessage to HTML conversion generates wrong HTML format
Issues with VCF to MSG Conversion
Issue with duplicate attachment after converting calendar mail
Folder Skipped While Converting PST to MBOX
MSG to MHTML - non-ASCII characters are transformed to question mark
The appointment content is improperly encoding
Issue while reading OLM File
MapiMessage.FromMailMessage throws Exception
Aspose.Email IgnoreSmtpAddressCheck does not allow %20 sequence
How to set MapiTask DateCompletion before Start Date
Unable to open EML file with MailMessage
Converting MSG to MHT throws exception
Newly added documentation pages and articles
Some new tips and articles have now been added into Aspose.Email for .NET documentation that may guide users briefly how to use Aspose.Email for performing different tasks like the followings.
Getting Total Number of Messages from MBox File
Export Microsoft Visio Drawing to PDF
Overview:Aspose.Email for .NET
Aspose.Email for .NET is a set of .net email components allowing developers to easily implement email functionality within their ASP.NET web applications, web services & Windows applications. It Supports Outlook PST, EML, MSG & MHT formats. It allows developers to work with SMTP, POP3, FTP & MS Exchange servers. It supports mail merge, iCalendar, customized header & body, header information, embedded files, Twitter & many more. It makes it easy to work with HTML or plain text emails & their attachments.
More about Aspose.Email for .NET
Homepage of Aspose.Email for .NET C#
Download Aspose.Email for .NET
Online documentation of Aspose.Email for .NET
#work with loading EML#list messages from Pop3Client#PST to MBOX conversion#load VCF contact#reading OLM file#VCF to MSG conversion#.NET Email API
1 note
·
View note
Text
I am getting the following error message when trying to use Sim Ripper and yes, I did download the most recent updated version. Details under the cut. I wanted to see if anyone else was having this issue before reporting it, or it is something I am doing.
See the end of this message for details on invoking just-in-time (JIT) debugging instead of this dialog box.
Exception Text System.NullReferenceException: Object reference not set to an instance of an object. at TS4SimRipper.Form1.UpdateSlotTargets(String& errorList) at TS4SimRipper.Form1.GetCurrentModel(Boolean skinOnly) at TS4SimRipper.Form1.GetCurrentModel() at TS4SimRipper.Form1.DisplaySim(SimData sim, SimOccult occultState) at TS4SimRipper.Form1.sims_listBox_SelectedIndexChanged(Object sender, EventArgs e) at System.Windows.Forms.ListBox.OnSelectedIndexChanged(EventArgs e) at System.Windows.Forms.ListBox.WmReflectCommand(Message& m) at System.Windows.Forms.ListBox.WndProc(Message& m) at System.Windows.Forms.NativeWindow.Callback(IntPtr hWnd, Int32 msg, IntPtr wparam, IntPtr lparam)
Loaded Assemblies mscorlib Assembly Version: 4.0.0.0 Win32 Version: 4.8.9139.0 built by: NET481REL1LAST_B
CodeBase: file:///C:/Windows/Microsoft.NET/Framework64/v4.0.30319/mscorlib.dll
TS4SimRipper Assembly Version: 1.0.0.0 Win32 Version: 1.0.0.0
CodeBase: file:///C:/Users/NATAL/Desktop/TS4SimRipper_3_14_2_0/TS4SimRipper.exe
System.Windows.Forms Assembly Version: 4.0.0.0 Win32 Version: 4.8.9075.0 built by: NET481REL1LAST_C
CodeBase: file:///C:/WINDOWS/Microsoft.Net/assembly/GAC_MSIL/System.Windows.Forms/v4.0_4.0.0.0__b77a5c561934e089/System.Windows.Forms.dll
System Assembly Version: 4.0.0.0 Win32 Version: 4.8.9139.0 built by: NET481REL1LAST_B
CodeBase: file:///C:/WINDOWS/Microsoft.Net/assembly/GAC_MSIL/System/v4.0_4.0.0.0__b77a5c561934e089/System.dll
System.Drawing Assembly Version: 4.0.0.0 Win32 Version: 4.8.9032.0 built by: NET481REL1
CodeBase: file:///C:/WINDOWS/Microsoft.Net/assembly/GAC_MSIL/System.Drawing/v4.0_4.0.0.0__b03f5f7f11d50a3a/System.Drawing.dll
s4pi.Package Assembly Version: 2002.10.2050.28502 Win32 Version: 2002.10.2050.28502
CodeBase: file:///C:/Users/NATAL/Desktop/TS4SimRipper_3_14_2_0/s4pi.Package.DLL
s4pi.Interfaces Assembly Version: 2002.10.2049.28497 Win32 Version: 2002.10.2049.28497
CodeBase: file:///C:/Users/NATAL/Desktop/TS4SimRipper_3_14_2_0/s4pi.Interfaces.DLL
s4pi.Settings Assembly Version: 2103.7.1628.20645 Win32 Version: 2103.7.1628.20645
CodeBase: file:///C:/Users/NATAL/Desktop/TS4SimRipper_3_14_2_0/s4pi.Settings.DLL
System.Core Assembly Version: 4.0.0.0 Win32 Version: 4.8.9139.0 built by: NET481REL1LAST_B
CodeBase: file:///C:/WINDOWS/Microsoft.Net/assembly/GAC_MSIL/System.Core/v4.0_4.0.0.0__b77a5c561934e089/System.Core.dll
System.Configuration Assembly Version: 4.0.0.0 Win32 Version: 4.8.9032.0 built by: NET481REL1
CodeBase: file:///C:/WINDOWS/Microsoft.Net/assembly/GAC_MSIL/System.Configuration/v4.0_4.0.0.0__b03f5f7f11d50a3a/System.Configuration.dll
System.Xml Assembly Version: 4.0.0.0 Win32 Version: 4.8.9032.0 built by: NET481REL1
CodeBase: file:///C:/WINDOWS/Microsoft.Net/assembly/GAC_MSIL/System.Xml/v4.0_4.0.0.0__b77a5c561934e089/System.Xml.dll
WindowsFormsIntegration Assembly Version: 4.0.0.0 Win32 Version: 4.8.9139.0 built by: NET481REL1LAST_B
CodeBase: file:///C:/WINDOWS/Microsoft.Net/assembly/GAC_MSIL/WindowsFormsIntegration/v4.0_4.0.0.0__31bf3856ad364e35/WindowsFormsIntegration.dll
PresentationFramework Assembly Version: 4.0.0.0 Win32 Version: 4.8.9139.0
CodeBase: file:///C:/WINDOWS/Microsoft.Net/assembly/GAC_MSIL/PresentationFramework/v4.0_4.0.0.0__31bf3856ad364e35/PresentationFramework.dll
WindowsBase Assembly Version: 4.0.0.0 Win32 Version: 4.8.9139.0 built by: NET481REL1LAST_B
CodeBase: file:///C:/WINDOWS/Microsoft.Net/assembly/GAC_MSIL/WindowsBase/v4.0_4.0.0.0__31bf3856ad364e35/WindowsBase.dll
PresentationCore Assembly Version: 4.0.0.0 Win32 Version: 4.8.9139.0 built by: NET481REL1LAST_B
CodeBase: file:///C:/WINDOWS/Microsoft.Net/assembly/GAC_64/PresentationCore/v4.0_4.0.0.0__31bf3856ad364e35/PresentationCore.dll
System.Xaml Assembly Version: 4.0.0.0 Win32 Version: 4.8.9139.0 built by: NET481REL1LAST_B
CodeBase: file:///C:/WINDOWS/Microsoft.Net/assembly/GAC_MSIL/System.Xaml/v4.0_4.0.0.0__b77a5c561934e089/System.Xaml.dll
PresentationFramework.Aero2 Assembly Version: 4.0.0.0 Win32 Version: 4.8.9032.0 built by: NET481REL1
CodeBase: file:///C:/WINDOWS/Microsoft.Net/assembly/GAC_MSIL/PresentationFramework.Aero2/v4.0_4.0.0.0__31bf3856ad364e35/PresentationFramework.Aero2.dll
Accessibility Assembly Version: 4.0.0.0 Win32 Version: 4.8.9032.0 built by: NET481REL1
CodeBase: file:///C:/WINDOWS/Microsoft.Net/assembly/GAC_MSIL/Accessibility/v4.0_4.0.0.0__b03f5f7f11d50a3a/Accessibility.dll
PresentationFramework-SystemXml Assembly Version: 4.0.0.0 Win32 Version: 4.8.9032.0
CodeBase: file:///C:/WINDOWS/Microsoft.Net/assembly/GAC_MSIL/PresentationFramework-SystemXml/v4.0_4.0.0.0__b77a5c561934e089/PresentationFramework-SystemXml.dll
protobuf-net Assembly Version: 2.0.0.668 Win32 Version: 2.0.0.668
CodeBase: file:///C:/Users/NATAL/Desktop/TS4SimRipper_3_14_2_0/protobuf-net.DLL
DDSPanel Assembly Version: 2002.10.2050.28504 Win32 Version: 2002.10.2050.28504
CodeBase: file:///C:/Users/NATAL/Desktop/TS4SimRipper_3_14_2_0/DDSPanel.DLL
s4pi.ImageResource Assembly Version: 2104.21.1540.19202 Win32 Version: 2104.21.1540.19202
CodeBase: file:///C:/Users/NATAL/Desktop/TS4SimRipper_3_14_2_0/s4pi.ImageResource.DLL
JIT Debugging To enable just-in-time (JIT) debugging, the .config file for this application or computer (machine.config) must have the jitDebugging value set in the system.windows.forms section. The application must also be compiled with debugging enabled.
For example:
When JIT debugging is enabled, any unhandled exception will be sent to the JIT debugger registered on the computer rather than be handled by this dialog box.
7 notes
·
View notes
Text


| 𝖓𝖊𝖔𝖓 𝖉𝖗𝖊𝖆𝖒 | CHAPTER 4
pairing; camboy!seokmin x female!reader
this chapter’s notes; camboy!au, university!au, camboy!seokmin, mentions of breeding!kink / impregnation!kink, dirty talk! 😗💕 A bit of a shorter chapter this week but it’s very seokmin is all I will say LMAO kdhfkdh Also I have a bit of a schedule change for next week but I’ll post a formal notice of that on... either tomorrow or Sunday! As always thanks for your support with ND 🥺💕 I’m trying to write it as if it were really Seokmin trying to cam so it’s a bit experimental and not as quick as the lil blurb I initially wrote 🤣 LOL but! enjoy ch 4 and I’ll see u tomorrow for inbox msgs! Have a good weekend! 💕
chapters; 1 - 2 - 3 - 4 - ?

“To be honest, I’m surprised you went through with paying for my lessons.”
Jihoon runs a hand through his freshly dyed hair; lips curving into a smirk when Seokmin pouts back at him. “And to already schedule our next session and pay for it too? I thought you were strugglin’ for cash? What happened?”
A blush paints across Seokmin’s cheeks as he sits across Jihoon in the slight older male’s studio. He’d, maybe, gotten a little ahead of himself out of excitement and paid for his next lesson as soon as he could and spent the remainder of what he’d made on buying snacks out of the vending machine on the way over.
“Yeeaaaah, I just… Uh, started picking up more shifts at my part-time jobs, is all. No biggie. I really wanted to polish my skills so I could start auditioning for some of the uni’s musicals ‘n stuff. I know we’re doing auditions soon so...” He scratches the nape of his neck shyly and Jihoon catches the way Seokmin avoids his stare.
“Just tell me you’re not dealing drugs for the money… Right?”
“What!? No! I mean, Joshua makes some good money selling weed but no, um, I’m too n-nervous for that… Haha...”
Jihoon narrows his eyes and turns to face his computer once more; tapping on an audio file before relaxing in his computer chair.
He’ll accept Seokmin’s answer for now - even if he is a little suspicious.
“Okay, well, let’s do one more run through and then I’ll let you go for today.”

Seokmin feels like he’s on cloud nine once he leaves Jihoon’s studio and even though he hasn’t done a camshow since the last, he feels a little more confident in his skills.
In both aspects.
Even if he’d been aided by alcohol the last time.
That’s fine, he tells himself, I just need to study what I was saying and just... Refine it. Maybe watch a few more videos and get the hang of it. I’ll be fine!
Which Seokmin finds much more embarrassing than he anticipates when he finally sits down in front of his computer, headphones on and eyes filled with determination when he presses ‘Play’ on the reuploaded audio stream.
‘...I’d cum so much inside of you… ‘n stretch you out so good…’
Christ, did I really sound like that?
‘...I wanna feel your pussy sucking my cock in deeper while I fuck my cum inside you like the filthy ‘lil cocksleeve that you are…’
Seokmin has to pause after a few more minutes; entire body breaking out into a cold sweat as he grimaces. He knew eventually he’d get used to it, but somehow listening to his own voice saying those things made him feel a little awkward.
Maybe he just wouldn’t rewatch them after he was finished.

You’re only three sentences away from finishing your paper when you decide to take a break - back arching away from your computer chair when a notification lights up your phone screen.
‘Dokyeom has gone live!’
‘Curious to see what you like… [AUDIO ONLY]’
Your lips form a surprised ‘o’ shape as you click on the notification and wait for the stream to load up.
He’d gotten a sudden spike in viewers with his last show but you’d been surprised when he hadn’t messaged you at all, much less done another stream since then.
Not that he owes me a response, you tell yourself.
“Hey everyone~”
His voice floats through your phone receiver and you feel your heart flutter at the airy, yet deepness of his voice.
You hated to admit it, but you’d rewatched his audio stream from last week a multitude of times and even saved it to your computer just in case he decided to delete it.
Anonymous4987395: what’s with the title?
NewUser89547: ur last vid was so hot omg
Your fingers hover above the keyboard, somewhat nervous about commenting.
“Oh, yeah, I was surprised at how popular it was actually… And it’s still getting viewed too, even though it’s just an audio recording. So thank you! I really appreciate it everyone~”
Anonymous283479: ur voice is sooo good it made me cum so fast…
Anonymous98957: can’t stop thinkin about u breeding me…
“Hmm… Breeding? What’s that?” Dokyeom responds in a drawl that has your toes curling against the floor and you can’t help but bite your lip and quickly type up a response before you change your mind.
b@d_dream: it’s like… getting off to the idea of not wearing a condom and cumming inside someone and the risk of getting them pregnant… or getting pregnant tbh… its like... popular with pet play and stuff 🥴
There’s a long pause on Seokmin’s end as he stares at your comment for a little longer trying to grasp what people wanted to hear from him.
Okay… Let’s see...
“Hmm… Okay~ Of course, my favourite ‘b@d_dream’ is really knowledgeable~ I should thank them for helping me out.” He finishes with a chuckle that sends you squirming in your seat.
“Interesting… I guess I might’ve ignited that interest since my last stream, huh? Me talking about how much I wanted to cum deep inside your pussy… But I bet it’d feel so good to feel me cumming inside you, cock throbbing and fucking you so deep…”
The comments and donations move faster than Seokmin can read or catch up to so he decides to focus on the stream for now before he loses his concentration.
Just 30 minutes and then I can figure out everything else, he tells himself.
Anonymous98756: god ur voice is so hot
Anonymous203948869: just thinkin about u ramming ur cock inside my pussy and fucking me like a bad girl gets me so wet...
Seokmin’s brain fizzles as he sits in his computer chair, mouth going dry when he’s unsure what to say next.
In a panic, he opens a side window and hurriedly pulls up a chat window.
Fuck, I’m so stupid!

Dokyeom: I’m so stupid, please help
b@d_dream: ??
Dokyeom: I don’t know what to say please please help
b@d_dream: lmaoooo about breeding?
Dokyeom: yes im so sorry
“Ah, my cock is so hard just thinking about it… I bet you’re already so wet, aren’t you? I could probably slide my cock right into your pussy right now...”
b@d_dream: mmmmm depends, but just talk about how much u wanna knock someone up? Thats basically it in a nutshell and i dont think u have time for specifics rn
“Mmm… Just thinking about my cum pouring out of your cunt is making me want to cum already…”
Dokyeom: fuck thanks and sorry, i owe u one once this is over i promise
b@d_dream: sure lol btw i can hear u typing so u better go

“Ah, I better cum inside your pretty ‘lil cunt a few times... Just to make sure you get nice ‘n pregnant, right? But you’ll be good and take all my cum, won’t you?”
You lick your lips as you listen to Dokyeom’s soft sighs and breathy moans; too engrossed in appreciating his voice to even get off.
It’s okay, I’ll just save the video again.
“Hmm... How would I fuck you? Depends, how do you want me to? I can fuck you from behind... Or would you want to see my face when I make you fall apart on my cock? I bet you’d be so pretty when you cum too... Mm, even prettier when you hold me against your body and make sure none of my cum leaks out of your pussy...”
NewUser8439579: oh my god please...
Anonymous974975: I’d ride u any time I get as long as u keep talking to me... can you say kitten?
“Ah, kitten?”
You feel goosebumps rise on your skin when he repeats it a few times to get used to it.
“Oh, does kitten want me to breed her ‘lil pussy? Mm... it’s just in your instinct to want it, huh? But it’s okay, I’ll give it to you... As many times as you want, kitten~”
Anonymous39847595: fuck I bet ur so hot...
NewUser934957: omg ikr...
“Haha, you think so? I get told I look good enough to be a model... Or is that too cocky of me to say? Especially since none of you know how I look~”
b@d_dream: I bet ur hot 😏
“Mm, maybe one day I’ll let you all see... So you can imagine me hovering above you when I fuck you. But only if you’re a good girl, y’know? Bad girls only get fucked from behind while I spank your pretty ass~”

Dokyeom ends his stream after 45 minutes and you rush to your computer to download the replay.
‘1 New Message’
You click on the notification; not surprised when you see it’s Dokyeom.
Dokyeom: I really owe you for earlier, is there anything I can do for you? I can record something for you... Like a private video? 😭 As a thank you.
b@d_dream: Oh uh you don’t really have to do that if you’re not comfortable, I don’t mind really!
Your entire body buzzes and you’re unsure what to tell him. You knew that if he recorded a video for you, he might ask for your name and you weren’t too sure if you wanted to give him that just yet.
But you also didn’t want to miss the chance of having a personalized audio recording just for yourself.
And before you can properly type up a response, Dokyeom beats you to the punch as his messages pop up on the screen.
Dokyeom: Actually I’ll do you one better
Dokyeom: How about we voice chat when you’re free? 30 minutes of your time and maybe you can help me out a bit more? We both gain something, ykwim? I can learn what you like since you’re more knowledgeable than me 😅
Your mouth hangs agape as you stare at his message.
Now you were really nervous but really excited.
b@d_dream: yeah sure, I'll check my schedule and let you know when I’m free! Don’t forget to bring a notepad 😉
Dokyeom: Can’t wait!

#seokmin smut#seventeen smut#svt smut#seokmin scenarios#seokmin imagines#seventeen imagines#svt imagines#seventeen scenarios#svt scenarios#dokyeom smut
290 notes
·
View notes
Note
Hi! I hope I'm not bothering you, but I love your mood board edits and was wondering if you could explain how you go about making/colouring them? I see lots of places to find gifs but turning them into a set is so hard. Thank you in advance!
hi! first of all thank you so much and second of all it’s not a bother at all! i am happy to give some of my own tips even if my explanation probably isn’t super helpful. i won’t give like a ps tutorial but below the cut (since i included example gifs, it’s VERY long) is my process for my latest jily aesthetic:
i keep track of all my ideas/sets in a spreadsheet (which i won’t show bc there’s a lot of info i’d have to blur/black out) but i always have a list of what scenes i need to gif/what gifs i’m editing and where i’m getting them from. i also include a couple extra ideas in case the gifs i have planned end up being too hard to color or don’t fit in the set. i’ve found it’s best/easiest to start w the list bc there is literally nothing worse than spending hours on a set and then not being able to complete it.
as for actually finding the material, i have a pretty healthy number of scene packs saved in my giffing folder, esp. for things i know i will gif frequently. most of the time i will peruse youtube, vimeo, and instagram for any aesthetic scenes. i also have a lot of gif packs saved specifically for the purpose of making mbs (usually i mix my own gifs w gif packs), if you msg me i’m happy to direct you to some gif packs i use regularly or you can check my #resources tag. a couple tips for finding material:
always opt for download when possible, i used to screen record and the difference when i switched to downloading was astronomical. (it’s easy to lose quality and esp if you’re on mac, quicktime duplicates frames so either you have to manually delete those extras or you get sort of choppy gifs when you load them into ps.)
always use 1080p or better, 720p will work in a pinch for 268px or 177px gifs since you can make up some of that resolution loss with sharpening, but don’t go any lower than that, just love yourself.
for pale sets, look for the right colors. i tend to look for scenes w high color contrast especially if it features poc so it’s easier to color without whitewashing, ie if the subject is a person then i look for light colored or blue/green/violet/white backgrounds. it’ll make your life wayyyyy easier. this also means if you’re making a set try to find scenes with already similar lighting bc you won’t have to work so hard to make it look cohesive.
here’s a quick rundown of what i do before coloring:
import all frames and save all the files in a folder together!!
play around with frame delay so all the gifs are moving at about the same speed, usually keep it between 0.03-0.05s
crop and resize gifs (i use 268x145 most of the time)
convert to timeline
when it comes to coloring it can be really hit or miss, i’ve recently gotten back into my groove but i was having sooo much trouble earlier this year. in general, don’t stress yourself out!! sometimes it’s easier to just find a new scene/gif (hence my list of extras!) than to try too hard to fit a gif into your set. i color all my gifs by scratch (ie no psds) but i tend to follow the same pattern, i’ll explain using these gifs/psd as an example since then i can also explain how to fix white-washing:


first off when you’re coloring gifs with poc always always always make a layer mask so you can compare the edited and unedited skin tones directly! i use the marquee tool to make a selection in the middle of the character’s face, select the folder of my adjustment layers, and hit ‘add vector mask’ (the third button from the left on the layers panel, it’s a white rectangle with a circle in it).
i almost always begin by using hue/saturation layers to highlight and delete certain colors. here i highlighted red and raised the lightness on yellow by a lot since it’s a very yellow scene. then i use a combination of brightness/contrast, levels, and curves layers to brighten the scene. here’s what i have now:

i add a gradient map set to black/white, change the blending to exclusion, and lower the opacity to between 5-10% (depending on the scene) to lighten the contrast further:

then i add back a little depth with selective color in neutrals and blacks:

now i have two main goals: 1. add contrast between the background and the subject, and 2. brighten the scene into a pale gif. to do this, i use color balance to tweak the color of the background, taking out the yellows. this step works best if there’s at least some shade difference between your subject and background, otherwise isolating the two will be impossible. here’s what i have after adding color balance:

i use hue/saturation to selectively highlight the background color. in this case i chose to adjust magenta and used the color picker (the first eyedropper on the left) to identify the exact shade i wanted to lighten. now i have a fairly neutral background and a colorful subject, which gives a sort of pale effect:

and now i use a curves layer and a selective color (white) layer to brighten further:


before i go further, i start fixing white-washing. keep in mind that some variance is normal since you are naturally changing the lighting of the scene; this gif shows it rlly clearly bc of how yellow and dim the lighting is, so some lightening is to be expected. however, both because the vector mask shows a lot of whitening and because i’ve giffed dev patel before and have a general idea of what he looks like in this type of lighting, i know what needs to be fixed, so i go back in under the psd/adjustment layers with a combination of selective color (red and neutral) and hue/saturation layers to darken his skin again:

now that some more contrast has been added in, i can go back to working on the psd and use curves and selective color to play around with the background again:

i use another hue/saturation layer and a black/white gradient to tone down oversaturation:


usually i leave those layers on top, so if i want to make any adjustments (like lightening the background more), i go in under those two. in this case i tweaked the whites and reduced the contrast a little to get this:


again, you can see his skin tone has changed from the original, but variation is to be expected given how much brighter the room is, the fact that i took out a lot of yellow lighting, and the brightening effect of the computer screen in front of him. some other things to keep in mind when coloring:
when you add layers to correct white-washing, you’re likely to end up with overly red/orange skin tones (red-washing). this can be fixed by upping cyans in the reds, desaturating/darkening the reds, or adding b/w or desaturation later on.
when in doubt, it’s better to be darker than lighter (the issue with white-washing is that it promotes colorism, and there is nothing inherently wrong with a darker skin tone) but really. just put in the effort to color poc correctly.
when changing the lighting a lot it helps to look at pictures of the subject in natural/bright lighting, since you get a better idea of what their normal skin tone is.
don’t try to squeeze all your selective color layers into one. you’ll get less grainy gifs if you separate them out and work one by one.
TURN OFF NIGHT SHIFT/NIGHT MODE! yes i KNOW it’s bad for your eyes (especially if you’re like me and gif at night, when the lighting outside isn’t changing every 20 seconds) but your gifs will look VERY different under f.lux or night mode compared to daytime screens. especially if you’re giffing at different times of day, blue light filters can really change the way your coloring appears. best to keep it consistent.
my sharpening settings vary depending on what i’m giffing but in general i do two layers of smart sharpen (500% with radius between 0.2-0.4, 10% with radius at 10px) and then gaussian blur at 2.5px and adjust the opacity so it’s somewhere between 15-20%. i try to strike a balance between smoothing out the graininess from selective color, and sharpening details like clothes and hair. here’s what i ended up with for the gif above:

then i rinse and repeat for the rest of the gifs in the set! i tend to start with the gifs that i know will be hardest to color, which is usually the darker ones (coloring is limited by how much i can brighten the scene) and those that include poc (again, limited by how much i can brighten and adjust the scene’s lighting without white-washing). then i check set cohesion as i go, using those first few gifs as benchmarks. once i have all 8 (or 9 or 10) gifs, i play around with composition and try to balance and vary the subject, colors, and composition of gifs next to each other. i go back and make a couple of adjustments here and there according to what i observe and what i think might improve the overall appearance.
and that’s pretty much it! i hope this was helpful, if you have other questions feel free to message me and i’d be happy to help/troubleshoot. happy giffing!
#Anonymous#*#resources#answered#sorry this was sO long but i hope it helped on the coloring end#tbh i exceeded my own expectations with the dev gif lol#yeahps#completeresources#chaoticresources#tutorial#coloring tutorial
55 notes
·
View notes
Text
UEFI hacking malware
Security researchers are alarmed: the already-notorious Trickbot malware has been spottied probing infected computers to find out which version of UEFI they're running. This is read as evidence that Trickbot has figured out how to pull off a really scary feat.
To understand why, you have to understand UEFI: a fascinating, deep, philosophical change to our view of computers, trust, and the knowability of the universe. It's a tale of hard choices, paternalism, and the race to secure the digital realm as it merges with the physical.
Computers were once standalone: a central processing unit that might be augmented by some co-processors for specialized processes, like a graphics card or even a math co-processor.
These co-pros were subordinate to the CPU though. You'd turn on the computer and it would read a very small set of hardcoded instructions telling it how to access a floppy disk or other storage medium for the rest of the boot sequence, the stuff needed to boot the system.
The hardwired instructions were in a ROM that had one job: wake up and feed some instructions to the "computer" telling it what to do, then go back to sleep. But there's a philosophical conundrum here.
Because the world of computing is adversarial and networked computing is doubly so: there are people who want your computer to do things that are antithetical to your interests, like steal your data or spy on you or encrypt all your files and demand ransom.
To stop this, you need to be able to examine the programs running on your computer and terminate the malicious ones. And therein lies the rub: when you instruct your computer to examine its own workings, how do you know if you can trust it?
In 1983, Ken Thompson (co-creator of C, Unix, etc) was awarded a Turing Award ("computer science's Nobel Prize"). He gave a fucking bombshell of an acceptance speech, called "Reflections on Trusting Trust."
https://www.cs.cmu.edu/~rdriley/487/papers/Thompson_1984_ReflectionsonTrustingTrust.pdf
Thompson revealed that he had created a backdoor for himself that didn't just live in Unix, but in the C compiler that people made to create new Unix systems.
Here's what that means: when you write a program, you produce "high-level code" with instructions like "printf("Hello, World!");". Once your program is done, you turn it into machine code, a series of much shorter instructions that your CPU understands ("mov dx, msg" etc).
Most programmers can't read this machine code, and even for those who can, it's a hard slog. In general, we write our code, compile it and run it, but we don't examine it. With nontrivial programs, looking at the machine code is very, very hard.
Compilers are treated as intrinsically trustworthy. Give 'em some source, they spit out a binary, you run the binary. Sometimes there are compiler bugs, sure, and compiler improvements can be a big deal. But compilers are infrastructure: inscrutable and forgotten.
Here's what Thompson did: he hid a program in his compiler that would check to see whether you were compiling an operating system or a compiler. If you were compiling an OS, it hid a secret login for him inside of it.
If you were compiling a compiler, it hid the program that looked for compilers or operating systems inside of it.
Think about what this means: every OS you compiled had an intentional security defect that the OS itself couldn't detect.
If you suspected that your compiler was up to no good and wrote your own compiler, it would be compromised as soon as you compiled it. What Thompson did was ask us to contemplate what we meant when we "trusted" something.
It was a move straight out of Rene Descartes, the reasoning that leads up to "I think therefore I am." Descartes' "Discourse on the Method" asks how we can know things about the universe.
He points out that sometimes he thinks he senses something but is wrong - he dreams, he hallucinates, he misapprehends.
If all our reasoning depends on the impressions we get from our senses, and if our senses are sometimes faulty, how can we reason at all?
Descartes wants a point of certainty, one thing he *knows* to be absolutely true. He makes the case that if you can be certain of one thing, you can anchor everything else to this point and build up a massive edifice of trustable knowledge that all hangs off of this anchor.
Thompson is basically saying, "You thought you had descartesed your way into a trustable computing universe because of the axiom that I would never poison your lowest-level, most fundamental tools.
"*Wrong*.
"Bwahahahaha."
(But, you know, in a nice way: an object lesson to serve as a wake-up call before computers fully merged with the physical world to form a global, species-wide digital nervous system whose untrustworthy low-level parts were foolishly, implicitly trusted).
But processors were expensive and computers were exploding. PCs running consumer operating systems like Windows and Mac OS (and more exotic ones like GNU/Linux and various Unices) proliferated, and they all shared this flawed security model.
They all relied on the operating system to be a faithful reporter of the computer's internals, and operated on the assumption that they could use programs supervised by the OS to detect and terminate malicious programs.
But starting in 1999, Ken Thompson's revenge was visited upon the computing world. Greg Hoglund released Ntrootkit, a proof-of-concept malware that attacked Windows itself, so that the operating system would lie to antivirus programs about what it was doing and seeing.
In Decartesspeak, your computer could no longer trust its senses, so it could no longer reason. The nub of trust, the piton driven into the mountainface, was made insecure and the whole thing collapsed. Security researchers at big companies like Microsoft took this to heart.
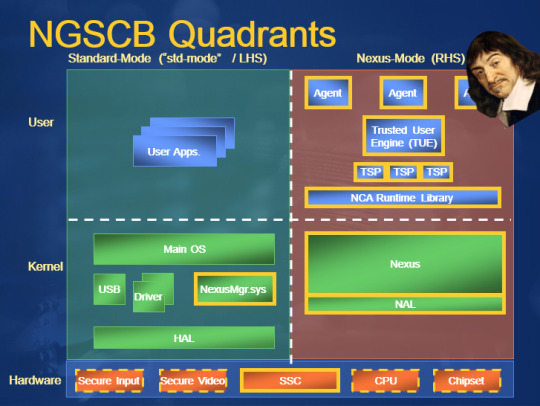
In 2002, Peter Biddle and his team from Microsoft came to EFF to show us a new model for computing: "Trusted Computing" (codenamed "Palladium").
https://web.archive.org/web/20020805211111/https://www.microsoft.com/presspass/features/2002/jul02/0724palladiumwp.asp
Palladium proposed to give computers back their nub of Descartesian certainty. It would use a co-processor, but unlike a graphics card or a math co-pro, it would run before the CPU woke up and did its thing.
And unlike a ROM, it wouldn't just load up the boot sequence and go back to sleep.
This chip - today called a "Secure Enclave" or a "Trusted Platform Module" (etc) - would have real computing power, and it would remain available to the CPU at all times.
Inside the chip was a bunch of cool cryptographic stuff that provided the nub of certainty. At the start of the boot, the TPM would pull the first stages of the boot-code off of the drive, along with a cryptographic signature.
A quick crypto aside:
Crypto is code that mixes a key (a secret known to the user) with text to produce a scrambled text (a "ciphertext") that can only be descrambled by the key.
Dual-key crypto has two keys. What one scrambles, the other descrambles (and vice-versa).
With dual-key crypto, you keep one key secret (the "private key") and you publish the other one (the "public key"). If you scramble something with a private key, then anyone can descramble it with your public key and know it came from you.
If you scramble it *twice*, first with your private key and then with your friend's public key, then they can tell it came from you (because only your private key's ciphertexts can be descrambled with your public key).
And *you* can be certain that only they can read it (because only their private key can descramble messages that were scrambled with their public key).
Code-signing uses dual-key crypto to validate who published some code.
Microsoft can make a shorter version of its code (like a fingerprint) and then you scramble it with its private key. The OS that came with your computer has a copy of MSFT's public key. When you get an OS update, you can descramble the fingerprint with that built-in key.
If it matches the update, then you know that Microsoft signed it and it hasn't been tampered with on its way to you. If you trust Microsoft, you can run the update.
But...What if a virus replaces Microsoft's public keys with its own?
That's where Palladium's TPM comes in. It's got the keys hardcoded into it. Programs running on the CPU can only ask the TPM to do very limited things like ask it to sign some text, or to check the signature on some text.
It's a kind of god-chip, running below the most privileged level of user-accessible operations. By design, you - the owner of the computer - can demand things of it that it is technically capable of doing, and it can refuse you, and you can't override it.
That way, programs running even in the most privileged mode can't compromise it.
Back to our boot sequence: the TPM fetches some startup code from the disk along with a signature, and checks to see whether the OS has been signed by its manufacturer.
If not, it halts and shows you a scary error message. Game over, Ken Thompson!
It is a very cool idea, but it's also very scary, because the chip doesn't take orders from Descartes' omnibenevolent God.
It takes orders from Microsoft, a rapacious monopolist with a history of complicity with human rights abuses. Right from that very first meeting the brilliant EFF technologist Seth Schoen spotted this (and made the Descartes comparison):
https://web.archive.org/web/20021004125515/http://vitanuova.loyalty.org/2002-07-05.html
Seth identified a way of having your cake and eating it too: he proposed a hypothetical thing called an "owner override" - a physical switch that, when depressed, could be used to change which public keys lived in the chip.
This would allow owners of computers to decide who they trusted and would defend them against malware. But what it *wouldn't* do is defend tech companies shareholders against the owner of the computer - it wouldn't facilitate DRM.
"Owner override" is a litmus test: are you Descartes' God, or Thompson's Satan?
Do you want computers to allow their owners to know the truth? Or do you want computers to bluepill their owners, lock them in a matrix where you get to decide what is true?
A month later, I published a multi-award-winning sf story called "0wnz0red" in Salon that tried to dramatize the stakes here.
https://www.salon.com/2002/08/28/0wnz0red/
Despite Seth's technical clarity and my attempts at dramatization, owner override did not get incorporated into trusted computing architectures.
Trusted computing took years to become commonplace in PCs. In the interim, rootkits proliferated. Three years after the Palladium paper, Sony-BMG deliberately turned 6m audio CDs into rootkit vectors that would silently alter your OS when you played them from a CD drive.
The Sony rootkit broke your OS so that any filename starting with $SYS$ didn't show up in file listings, $SYS$ programs wouldn't show up in the process monitor. Accompanying the rootkit was a startup program (starting with $SYS$) that broke CD ripping.
Sony infected hundreds of thousands of US gov and mil networks. Malware authors - naturally enough - added $SYS$ to the files corresponding with their viruses, so that antivirus software (which depends on the OS for information about files and processes) couldn't detect it.
It was an incredibly reckless, depraved act, and it wasn't the last. Criminals, spies and corporations continued to produce rootkits to attack their adversaries (victims, rival states, customers) and trusted computing came to the rescue.
Today, trusted computing is widely used by the world's largest tech companies to force customers to use their app stores, their OSes, their printer ink, their spare parts. It's in medical implants, cars, tractors and kitchen appliances.
None of this stuff has an owner override. In 2012, I gave a talk to Google, Defcon and the Long Now Foundation about the crisis of owner override, called "The Coming Civil War Over General Purpose Computing."
https://memex.craphound.com/2012/08/23/the-coming-civil-war-over-general-purpose-computing/
It proposed a way that owner override, combined with trusted computing, could allow users to resist both state and corporate power, and it warned that a lack of technological self-determination opened the door to a parade of horribles.
Because once you have a system that is designed to override owners - and not the other way around - then anyone who commands that system can, by design, do things that the user can't discern or prevent.
This is the *real* trolley problem when it comes to autonomous vehicles: not "who should a car sacrifice in a dangerous situation?" but rather, "what happens when a car that is designed to sometimes kill its owner is compromised by Bad Guys?"
https://this.deakin.edu.au/self-improvement/car-wars
The thing is, trusted computing with an owner override is pretty magical. Take the Introspection Engine, a co-processor in a fancy Iphone case designed by Edward Snowden and Bunnie Huang. It's designed to catch otherwise undetectable mobile malware.
https://www.tjoe.org/pub/direct-radio-introspection/release/2
You see, your phone doesn't just run Ios or Android; the part that interfaces with the phone system - be baseband radio - runs an ancient, horribly insecure OS, and if it is infected, it can trick your phone's senses, so that it can no longer reason.
The Introspection Engine is a small circuit board that sandwiches between your phone's mainboard and its case, making electrical contact with all the systems that carry network traffic.
This daughterboard has a ribbon cable that snakes out of the SIM slot and into a slightly chunky phone case that has a little open source hardward chip with fully auditable code and an OLED display.
This second computer monitors the electrical signals traveling on the phone's network buses and tells you what's going on. This is a user-accessible god-chip, a way for you to know whether your phone is hallucinating when it tells you that it isn't leaking your data.
That's why it's called an "Introspection Engine." It lets your phone perch at an objective remove and understand how it is thinking.
(If all this sounds familiar, it's because it plays a major role in ATTACK SURFACE, the third Little Brother book)
https://attacksurface.com
The reason the Introspection Engine is so exciting is that it is exceptional. The standard model for trusted computing is that it treats everyone *except* the manufacturer as its adversary - including you, the owner of the device.
This opens up many different sets of risks, all of which have been obvious since 1999's Ntrootkit, and undeniable since 2005's Sony Rootkit.
I. The manufacturer might not have your interests at heart.
In 2016, HP shipped a fake security update to its printers, tricking users into installing a system that rejected their third-party ink, forcing them to pay monopoly prices for HP products.
https://www.eff.org/deeplinks/2020/11/ink-stained-wretches-battle-soul-digital-freedom-taking-place-inside-your-printer
II. An insider at the company may not have your interests at heart.
Multiple "insider threat" attacks have been executed against users. Employees at AT&T, T-Mobile, even Roblox have accepted bribes to attack users on behalf of criminals.
https://www.vice.com/en/article/qj4ddw/hacker-bribed-roblox-insider-accessed-user-data-reset-passwords
III. A government may order the company to attack its users.
In 2017 Apple removed all working VPNs from its Chinese app stores, as part of the Chinese state's mass surveillance program (1m members of religious minorities were subsequently sent to concentration camps).
Apple's trusted computing prevents users from loading apps that aren't in its app stores, meaning that Apple's decisions about which apps you can run on your Iphone are binding on you, even if you disagree.
https://www.reuters.com/article/us-china-apple-vpn/apple-says-it-is-removing-vpn-services-from-china-app-store-idUSKBN1AE0BQ
IV. Third parties may exploit a defect in the trusted computing system and attack users in undetectable ways that users can't prevent.
By design, TPMs can't be field updated, so if there's a defect in them, it can't be patched.
Checkm8 exploits a defect in eight generations Apple's mobile TPM. It's a proof-of-concept released to demonstrate a vulnerability, not malware (thankfully).
https://checkm8.info/
But there have been scattered, frightening instances of malware that attacks the TPM - that suborns the mind of God so that your computer ceases to be able to reason. To date, these have all been associated with state actors who used them surgicially.
State actors know that the efficacy of their cyberweapons is tied to secrecy: once a rival government knows that a system is vulnerable, they'll fix it or stop using it or put it behind a firewall, so these tools are typically used parsimoniously.
But criminals are a different matter (and now, at long last, we're coming back to Trickbot and UEFI) (thanks for hanging in there).
UEFI ("You-Eff-Ee") is a trusted computing that computer manufacturers use to prevent unauthorized OSes from running on the PCs they sell you.
Mostly, they use this to prevent malicious OSes from running on the hardware they manufacture, but there have been scattered instances of it being used for monopolistic purposes: to prevent you from replacing their OS with another one (usually a flavor of GNU/Linux).
UEFI is god-mode for your computer, and a compromise to it would be a Sony Rootkit event, but 15 years later, in a world where systems are more widespread and used for more critical applications from driving power-plants to handling multimillion-dollar transactions.
Trickbot is very sophisticated malware generally believed to be run by criminals, not a government. Like a lot of modern malware, there's a mechanism for updating it in the field with new capabilities - both attacks and defenses.
And Trickbot has been observed in the wild probing infected systems' UEFI. This leads security researchers to believe that Trickbot's authors have figured out how to compromise UEFI on some systems.
https://www.wired.com/story/trickbot-botnet-uefi-firmware/
Now, no one has actually observed UEFI being compromised, nor has anyone captured any UEFI-compromising Trickbot code. The thinking goes that Trickbot only downloads the UEFI code when it finds a vulnerable system.
Running in UEFI would make Trickbot largely undetectable and undeletable. Even wiping and restoring the OS wouldn't do it. Remember, TPMs are designed to be unpatchable and tamper-resistant. The physical hardware is designed to break forever if you try to swap it out.
If this is indeed what's going on, it's the first instance in which a trusted computing module was used to attack users by criminals (not governments or the manufacturer and its insiders). And Trickbot's owners are really bad people.
They've hired out to the North Korean state to steal from multinationals; they've installed ransomware in big companies, and while their footprint has waned, they once controlled 1,000,000 infected systems.
You can check your UEFI to see if it's vulnerable to tampering:
https://eclypsium.com/2019/10/23/protecting-system-firmware-storage/
and also determine whether it has been compromised:
https://eclypsium.com/2020/10/14/protecting-your-organizations-from-mosaicregressor-and-other-uefi-implants/
But this isn't the end, it's just getting started. As Seth Schoen warned us in 2002, the paternalistic mode of computing has a huge, Ken Thompson-shaped hole in it: it requires you trust the benevolence of a manufacturer, and, crucially, they know you don't have a choice.
If companies knew that you *could* alter whom you trusted, they would have to work to earn and keep your trust. If governments knew that ordering a company to compromise on TPMs, they'd understand that their targets would simply shift tactics if they made that order.
Some users would make foolish decisions about whom to trust, but they would also have recourse when a trusted system was revealed to be defective. This is a fight that's into its third decade, and the stakes have never been higher.
Sadly, we are no closer to owner override than we were in 2002.
23 notes
·
View notes